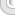Using
your Linux as a Router
 
This chapter is dedicated to those who would like to setup a linux router.
What does a router do you ask? Well, it's useful if you have a home network
with only one static ip address from your isp. It allows you to basically
turn that one ip address into as many as you need so all the computers
on your network can use the internet.
You do have one other choice, go out to a store like Best Buy and buy
a hardware router for about $180. These can be configured from a pc via
telnet which makes them nice. Also, they come with 4 open ports on them
so if you've been considering buying a new hub, it's already built into
the router. With the linux router, you'll need two NIC's and a hub. As
you can see, it may be more cost effective to just buy the hardware router
unless you got an old pentium 100 laying around collecting dust. Technically,
you don't even need a monitor, keyboard, or mouse hooked up to it to do
it's job.
One nice thing about the linux router as opposed to a hardware router,
it can be more than a router. You can also setup a firewall. In fact,
you use the firewall software IPCHAINS to setup the box as a router, so,
with just a bit of tinkering, you have a full fledged firewall as well.
A firewall is probably not required for the average setup since I'm assuming
you will be using lan addresses on your host pc's instead of internet
addresses, otherwise, what's the point in setting this up? The reason
it would not be required with lan addresses is that they cannot be seen
on the internet.
Also, you can use this box for other things such as a web or ftp server.
These will no doubt follow in later chapters.
The only other requirement is that you have Networking setup from the
Networking chapter.
Here is a basic diagram of a simple lan with a router to the internet.
It illustrates a dsl modem but cable modems work just the same way.

The first thing to do is install IPCHAINS. Unpack
it and type the following
make all
make install
Next, after you have physically installed the second nic
into the machine, recompile the kernel with the proper nic drivers compiled
as modules. As explained in networking, it's best to have pci nic's because
they don't require any configuration.
Also, make sure the following options are compiled into
the kernel as well:
sysct1 (found in general setup)
network firewalls (all the rest are in networking options)
advanced router
verbose route monitoring
firewalling
masquerading
icmp masq
optimize as router
syncookie support
Now, like in networking, modify
the /etc/modules.conf and add in your NIC's. You should make eth0 the
card that will be connected to the internet(modem) and eth1 the card that
will be connected to the lan. After this is complete, run depmod
Upon reboot, if linux should complain that the /etc/modules.conf
file is newer than the /lib/modules/X.X.XX/modules.dep file, use vi to
edit the modules.dep file and add a space or a blank line and then
save the file. This will cure the problem.
Next, cut and paste the following and save it into a file
called /etc/init.d/firewall
Do a chmod 755 /etc/init.d/firewall to make this
executable.
The parts in red are the only options that you will need
to modify.
#!/bin/sh
# A simple example of ipchains saved as /etc/init.d/firewall
# Load required ip_masq modules (FTP included here)
/sbin/depmod -a
/sbin/modprobe ip_masq_ftp
# Enable IP forwarding
echo "1" > /proc/sys/net/ipv4/ip_forward
# Assign external IP variables (to the internet, the ip your isp
assigned you)
extip="123.456.789.012"
extif="eth0"
# Assign internal IP variables (to the lan)
intif="eth1"
intnet="192.168.0.0/24"
# The address above will make it possible to use 192.168.X.X on your lan
where X.X are any numbers you choose form 0 to 255
# Initialize MASQ timeout and standard chains
ipchains -M -S 7200 10 60
ipchains -F input
ipchains -P input REJECT
ipchains -F output
ipchains -P output REJECT
ipchains -F forward
ipchains -P forward DENY
# Setup input policy
# local interface, local machines, going anywhere is valid
ipchains -A input -i $intif -s $intnet -d 0.0.0.0/0 -j ACCEPT
# reject IP spoofing where external computer claims to be a local
ipchains -A input -i $extif -s $intnet -d 0.0.0.0/0 -l -j REJECT
# allow external access via external interface
ipchains -A input -i $extif -s 0.0.0.0/0 -d $extip/32 -j ACCEPT
# loopback interface is valid
ipchains -A input -i lo -s 0.0.0.0/0 -d 0.0.0.0/0 -j ACCEPT
# Setup output policy
# all outgoing traffic is allowed
ipchains -A output -i $intif -s 0.0.0.0/0 -d $intnet -j ACCEPT
# prevent traffic for local network from using external interface
ipchains -A output -i $extif -s 0.0.0.0/0 -d $intnet -l -j REJECT
# prevent traffic from local network from using external interface
ipchains -A output -i $extif -s $intnet -d 0.0.0.0/0 -l -j REJECT
# anything else can go out
ipchains -A output -i $extif -s $extip/32 -d 0.0.0.0/0 -j ACCEPT
# loopback interface is valid
ipchains -A output -i lo -s 0.0.0.0/0 -d 0.0.0.0/0 -j ACCEPT
# Setup forwarding policy
# Masquerade local net traffic to anywhere
ipchains -A forward -i $extif -s $intnet -d 0.0.0.0/0 -j MASQ
Editing
/etc/init.d/network
#! /bin/sh
#
# network Establish the network connection.
#
# Version: @(#)network 2.2 19-Apr-1999 miquels@cistron.nl
#
IPV4_FORWARD=1
case "`uname -r`" in
2.0.*) ADDROUTE="yes" ;;
*) ADDROUTE="" ;;
esac
# Configure the loopback device.
ifconfig lo 127.0.0.1
[ "$ADDROUTE" ] && route add -net 127.0.0.0 dev lo
# Configure the ethernet device or start SLIP/PPP below (notice
the addition of a 0 after IPADDR, NETWORK, and BROADCAST).
IPADDR0="123.456.789.012" # Your IP
address.
NETMASK="255.255.255.224" # Your netmask.
NETWORK0="192.168.1.0" # Your network
address.
BROADCAST0="192.168.1.255" # Your
broadcast address (blank if none).
GATEWAY="123.456.789.012" # Your gateway address.
ifconfig eth0 ${IPADDR0} netmask ${NETMASK}
broadcast ${BROADCAST0}
[ "$ADDROUTE" ] && route add -net ${NETWORK0}
[ "$GATEWAY" ] && route add default gw ${GATEWAY}
#Stuff added by tom for masquerading
IPADDR1="192.168.0.1"
NETWORK1="192.168.1.1"
BROADCAST1="192.168.2.255"
ifconfig eth1 ${IPADDR1} netmask ${NETMASK} broadcast
${BROADCAST1}
[ "$ADDROUTE" ] && route add -net ${NETWORK1}
[ "$ADDROUTE" ] && route add default gw ${GATEWAY}
/etc/init.d/firewall
/sbin/ipchains -A forward -s 192.168.0.0/24 -j MASQ
That should do it. Reboot the machine and give it a test. Ping the loopback,
eth1, and eth2 addresses. Ping a www address to make sure dns is working.
On your host computers, assign them ip addresses in the 192.168.X.X
range with matching NETMASKS (subnets) as selected above. The gateway
device should be 192.168.0.1 if you didn't change anything from above. You
put in the dns addresses that your isp gave you (If you are using linux
machines as hosts instead of windows machines, the dns info goes in /etc/resolv.conf
just like in the networking chapter. Also, it's not resolve.conf, it's
resolv.conf without the 'e').
That should do it, there shouldn't be any problems. Re-check for typos
if your having problems.
|